What is the topic?
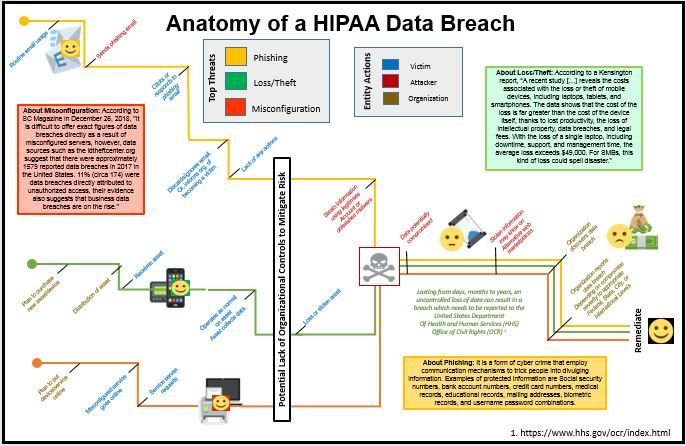
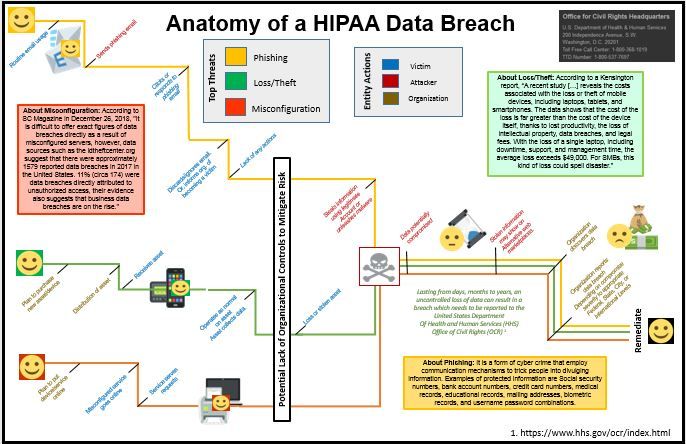
The topic under investigation is to some of the literature on top threats which can cause a HIPAA data breach and condense the material into a qualitative visualization. Examining the United States Department of Human Services Office of Civil Rights' "Wall of Shame" indicates some of the top threats which ultimately cause data breaches potentially leading to incurred fines, reputational damage, and other financial burdens.
What is the data set?
The data set is the United States Department of Human Services Office of Civil Rights' "Wall of Shame."
What are the visual decisions you made?
The visual decisions include how to tell the multiple threat stories in one visualization. On searching for predecessors, I ran across this Christmas Story visualization posted by Stephen Smith. I liked how the timeline showed many different paths and how they were unique but yet related in parts.
What were the original sketches and iterations?
Originally, I created three unique views of different threats as seen in: Phishing, Misconfiguration, and Loss/Theft.
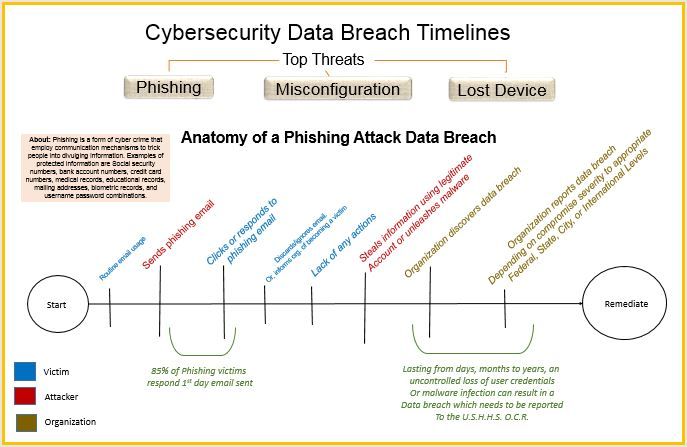
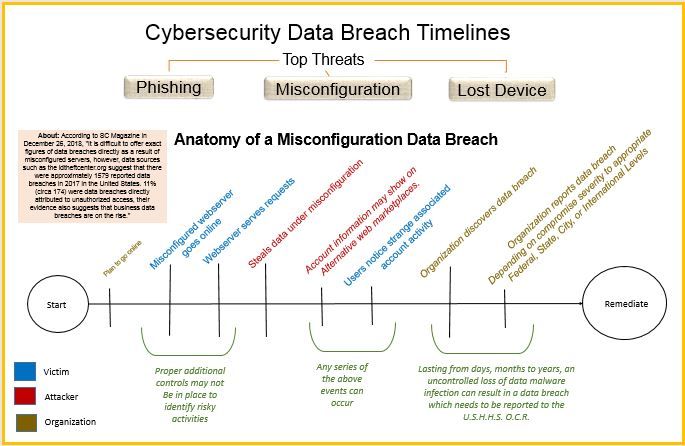
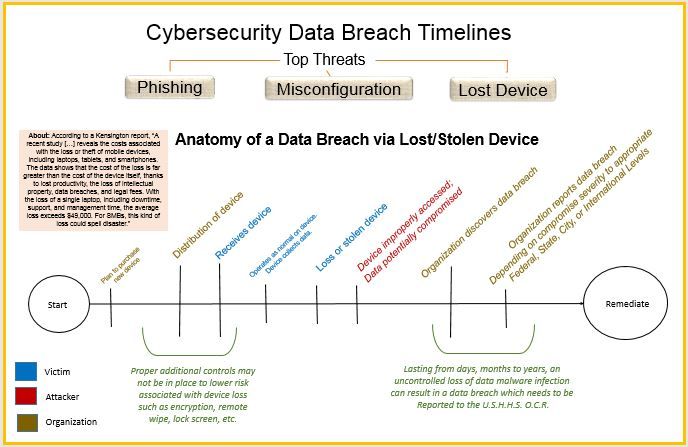
After careful analysis and considering the feedback given by my instructors and colleagues, my next iteration included the following: